- Apr 25, 2015
- 1,845
- 2
- 2,199
- 327
So you login to your Linux box and are using my Linux incident response script.
After you cat the accepted logins file:
You find all sorts of shit displaying your IP address like:
Now, since we know our IP is 172.22.10.10 and that likely is filling the whole damn log file, how about we grep our file without or IP address?
This should list all the different IP addresses logging in, but what if our coworker is logging in often?
Maybe we see
Simple!
Now let's say on July 26 everyone in our office decided to celebrate the non-existent "SSH Login To Flood The Logs" holiday and you're just like "Well, fuck July 26."
Okay, so then we are finding the attacker probably compromised the system right around July 23, since our logs show "Jul 23" we can just grep those!
Man, I just want ALL the logs from July now - cake!
After arranging our logs how we want them, we isolate the offending IP address to logging in at absurd times. For example, no one should be in SSH outside of 9 am to 5 pm. This narrows down logs to sort! My below egrep is not 9-5, you can figure out the military time and set that up. I could but am not doing everything for you; learn some.
With our IP address in hand, 172.22.13.37 we want to know more about this host on our Windows network.
Launch PowerShell or cmd (Command Prompt) and obviously replace the offender's fake IP below:
This may take about 10-30 seconds depending on your Windows network, a good result looks like this:

Assuming we are running modern Windows systems on our network and they are joined to our domain (we are a network admin), we are going to want to remote into this machine to perform further evidence collection and start this log analysis process all over again except dealing with a Windows workstation, not the Linux one as exampled above.
None of this information is "real", this is all sample data for educational purposes only.
---
To continue your investigation, I recommend using Active Directory PowerShell Module, consider downloading RSAT then reboot if you cannot get the Get-ADComputer PowerShell working:
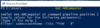
Do not forget you may use
We can do a one-liner for example:
Now we at least know the machine is for sure in our AD, that we should be admin of:
Should return:
Now we can enter into a remote session:
Change STAFFXX and AdminAccountNameGoesHere as obvious.
Any questions at all? I would love to answer them.
Hopefully this has been educational to anyone curious how the investigation of some type of attack goes, or at least can go. There are many many ways an investigation can go, sometimes even requiring referencing Microsoft Windows' Shadow Copy (VSS) if someone tries hiding evidence of compromise.
The evidence trail will continually trace backwards until we reach the attacker's original IP/proxy/VPN, either way there are trails.
After you cat the accepted logins file:
Code:
cd /evidence/misc
cat accepted_passwordYou find all sorts of shit displaying your IP address like:
Accepted password for donkeywizard from 172.22.10.10 port 65XXX ssh2
Now, since we know our IP is 172.22.10.10 and that likely is filling the whole damn log file, how about we grep our file without or IP address?
Code:
grep -v "172.22.10.10" accepted_passwordThis should list all the different IP addresses logging in, but what if our coworker is logging in often?
Maybe we see
Accepted password for llamatoucher from 172.22.10.21 port 65XXX ssh2
Simple!
Code:
grep -v "172.22.10.10\|172.22.10.21" accepted_passwordNow let's say on July 26 everyone in our office decided to celebrate the non-existent "SSH Login To Flood The Logs" holiday and you're just like "Well, fuck July 26."
Code:
grep -v "172.22.10.10\|172.22.10.21\|Jul 26" accepted_passwordOkay, so then we are finding the attacker probably compromised the system right around July 23, since our logs show "Jul 23" we can just grep those!
Code:
grep "Jul 23" accepted_password | grep -v "172.22.10.10\|172.22.10.21"Man, I just want ALL the logs from July now - cake!
Code:
grep "Jul " accepted_passwordAfter arranging our logs how we want them, we isolate the offending IP address to logging in at absurd times. For example, no one should be in SSH outside of 9 am to 5 pm. This narrows down logs to sort! My below egrep is not 9-5, you can figure out the military time and set that up. I could but am not doing everything for you; learn some.
Code:
egrep " 0[0-7]:| 1[3-9]:| 2[0-4]:" accepted_passwordWith our IP address in hand, 172.22.13.37 we want to know more about this host on our Windows network.
Launch PowerShell or cmd (Command Prompt) and obviously replace the offender's fake IP below:
Code:
nbtstat -a 172.22.13.37 | findstr "UNIQUE"This may take about 10-30 seconds depending on your Windows network, a good result looks like this:
Assuming we are running modern Windows systems on our network and they are joined to our domain (we are a network admin), we are going to want to remote into this machine to perform further evidence collection and start this log analysis process all over again except dealing with a Windows workstation, not the Linux one as exampled above.
None of this information is "real", this is all sample data for educational purposes only.
---
To continue your investigation, I recommend using Active Directory PowerShell Module, consider downloading RSAT then reboot if you cannot get the Get-ADComputer PowerShell working:
Do not forget you may use
help Get-ADComputer.We can do a one-liner for example:
Code:
Get-ADComputer -Filter "samAccountName -like '*TAFFXX$'"Now we at least know the machine is for sure in our AD, that we should be admin of:
Code:
Test-WsMan STAFFXXShould return:
wsmid : http://schemas.dmtf.org/wbem/wsman/identity/1/wsmanidentity.xsd
ProtocolVersion : http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd
ProductVendor : Microsoft Corporation
ProductVersion : OS: 0.0.0 SP: 0.0 Stack: 3.0
Now we can enter into a remote session:
Code:
Enter-PSSession -ComputerName STAFFXX -Credential AdminAccountNameGoesHereAny questions at all? I would love to answer them.
Hopefully this has been educational to anyone curious how the investigation of some type of attack goes, or at least can go. There are many many ways an investigation can go, sometimes even requiring referencing Microsoft Windows' Shadow Copy (VSS) if someone tries hiding evidence of compromise.
The evidence trail will continually trace backwards until we reach the attacker's original IP/proxy/VPN, either way there are trails.