Supervisor
Administrator
- Apr 27, 2015
- 1,863
- 2,546
- 335
As you may know, the Yubikey is a small device with a lot of features also including support for gpg keys and the abillity to be used for ssh-login into remote servers.
In this tutorial I will provide step-by-step instructions on how to accomplish that.
When beeing finished, the private keys will be on the Yubikey and you will only be able to login with this key. The keys therefore cannot be stolen even if you are hacked.
Lets get started. Everything you need to type is bold, everything you need to change depending on your setup is marked red. Screenshots are in german language, but I guess you can figure out the important stuff.
Some more screenshots can be found in the second post.
In this tutorial I will provide step-by-step instructions on how to accomplish that.
When beeing finished, the private keys will be on the Yubikey and you will only be able to login with this key. The keys therefore cannot be stolen even if you are hacked.
Lets get started. Everything you need to type is bold, everything you need to change depending on your setup is marked red. Screenshots are in german language, but I guess you can figure out the important stuff.
For a better understanding of KEY_ID:
KEY_ID is the main key with all subkeys in it
KEY_ID_1 is the first subkey, used for signing
KEY_ID_2 is used for the subkey encryption
KED_ID_3 is used for the subkey authentication
You may type gpg --list-keys, they will each have letters \[C\], \[S\], \[E\], \[A\] wich are the exact same order as above.
KEY_ID is the main key with all subkeys in it
KEY_ID_1 is the first subkey, used for signing
KEY_ID_2 is used for the subkey encryption
KED_ID_3 is used for the subkey authentication
You may type gpg --list-keys, they will each have letters \[C\], \[S\], \[E\], \[A\] wich are the exact same order as above.
- Download & install GPG4Win https://www.gpg4win.org/download.html
- Create Keys from Powershell - type in the following commands and make personal choices if asked
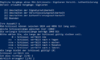
- gpg --expert --full-gen-key
- choose RSA, choise 8
- choose Cert only
- set 2048 or 4096 as length
- set a passphrase
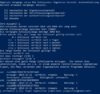
- gpg --expert --edit-key KEY_ID
- We will add three subkeys, one at a time for Sign, Verify and Encrypt (so do the following three times)
- addkey
- Choose Auth, Sign, Encrypt seperatly
- choose length of 2048
- When done creating the three subkeys, hit save
- gpg --expert --full-gen-key
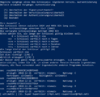
- Backup secret keys
- gpg --export-secret-key --armor KEY_ID > cert.KEY_ID.key
- For exporting the subkeys, please note the ! behind the KEY_ID
- gpg --export-secret-subkeys --armor KEY_ID_1! > sign.KEY_ID.key
- gpg --export-secret-subkeys --armor KEY_ID_2! > encr.KEY_ID.key
- gpg --export-secret-subkeys --armor KEY_ID_3! > auth.KEY_ID.key
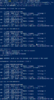
- Save the ssh-key - you can always generate it later using the public key
- gpg --export-ssh-key KEY_ID > ssh.KEY_ID.pem
- You may want to upload your public key to a keyserver so you can always get a hold of it or share it
- gpg --keyserver hkp://pool.sks-keyservers.net --send-keys KEY_ID
- Lastely we need to save the revoke-key to make sure we can invalidate the certificate once we lost it or dont use it any longer - copy the KEY_ID.rev from %appdata%\gnupg\openpgp-revocs.d\ to the location where you have the other keys backed up
- Move your keys to the Yubikey - make sure it is plugged in by now.
- gpg --expert --edit-key
- key KEY_ID_1
- keytocard
- key KEY_ID_1
- key KEY_ID_2
- keytocard
- key KEY_ID_2
- key KEY_ID_3
- keytocard
- key KEY_ID_3
- save
- Change your card pin and admin pin and reset phrase - make sure you don't loose them! You will need the Pin every time you want to ssh into a server later. We will also edit some stuff as Cardholder name, sex and so on. That is not needed though
- gpg --expert --card-edit
- admin
- name
- sex
- lang
- passwd
- quit
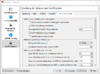
- Get Putty ready to accept GPG4Win - Check the Box "Attempt authentication using Pageant" in Connection-SSH-Auth (of course thats all in Putty)
- Open Kleopatra (it got installed with GPG4Win)
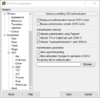
- open Settings - Setup Kleopatra - GnuPG-System - Secret keys
- tick the boxes SSH-Support enable, PuTTY-Support enable
- There is one inconvinience with the entire setup - we need a service running when we want to ssh into a server and use our Yubikey. Its called gpg-connect-agent.exe. You can either start it every time you need it, manually or you just create a shortcut and move it into your autostart directory so it automatically starts up every time with windows. Also, when you have troubles, simply restart the program.j
- create a shortcut to "C:\Program Files (x86)\GnuPG\bin\gpg-connect-agent.exe" /bye
- move it to your autostart in "%appdata%\Microsoft\Windows\Start Menu\Programs\Startup" or start it manually - your choice
- Testing time
- upload the content of your ssh.KEY_ID.pem to the authorized_keys file on your linux server
- it is located it the user directory -> .ssh/authorized_keys
- now lets test the connection - therefore, login to the ssh server - it should ask you to enter the pin for your smartcard (your YubiKey), enter and you're in
- if you encounter any problems feel free to reply and I think we should get it working
- After making sure you have a backup of your keys, its time to delete the private key from your computer so only the Yubikey has it now.
- gpg --delete-secret-key KEY_ID
- If you want to, you may also delete your public key - thats not needed though
- gpg --delete-key KEY_ID
Some more screenshots can be found in the second post.
Last edited: