- Apr 25, 2015
- 1,844
- 2
- 2,197
- 327
Follow this video here first:
Copy these snippets as needed..
SERVER COMMANDS - Navigate to your Command Prompt and type "powershell" [enter] first.
Find your IP from Netstat, but the next command is more automatic.
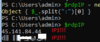
If you see two IP addresses pulled from active RDP connections, do not whitelist with the next command. Otherwise, carry on!
Cool trick to get your server IP:
According to this here, Microsoft recommends.
For details, see Enable-PSRemoting and Enable-WSManCredSSP.
The server should be ready to go, for sure.
---
The client also requires some specific configurations like this:
Open a Windows PowerShell session as Administrator.
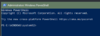
Make sure your current network profile is set to private, simply copy/paste:
Open gpedit.msc
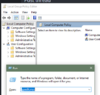
Go to Local Computer Policy > Computer Configuration > Administrative Templates > System > Credentials Delegation
Enable "Allow delegating fresh credentials"
Enable "Allow delegating fresh credentials with NTLM-only server..."
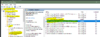
In both of the above policy settings you enabled, add this:
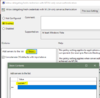
wsman/*
Apply said changes, you should be all set...
Any errors? Let me know right away and I will help!! Just reply to this thread..
Skip the below, don't gaf to work w/ secedit or keep debugging through regedit messin'
---NONE OF THE FOLLOWING WORKS... HINTTTTTTTTTTTTTTTTTT::: SKIP TO THE NEXT POST IN THIS THREAD!! Just mad scientist crap is below on this specific post.. - I GIVE UP, SKIP IT.. should work fine without the below, also not responsible if it breaks ur pc lol ---
Time to edit your silly-stuff just in case, same PowerShell entry area:
Not working, download RSAT:
Download version WindowsTH-RSAT_WS_1803-x64.msu or latest - launch - install.
Continue, accept, etc.
You will now have access to..
Group Policy editing, whoo! Turns out this only works if ur actually in a domain, many ppl probably r not lel. Need forest.. AD/DC
...
Get-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 1
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 2
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 3
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 4
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 5
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 6
Set-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 1 -Value "wsman/*"
Get-ItemProperty -Path HKLM:\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\
Remove-ItemProperty -Path HKLM:\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 1
Remove-ItemProperty -Path HKLM:\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 2
Copy these snippets as needed..
SERVER COMMANDS - Navigate to your Command Prompt and type "powershell" [enter] first.
Find your IP from Netstat, but the next command is more automatic.
Code:
netstat -nabo | findstr 3389 | findstr EST
Code:
$rdpIP = netstat -nabo | findstr 3389 | findstr EST | ForEach-Object { $_.split(" ")[10] } | ForEach-Object { $_.split(":")[0] }
$rdpIP
#Make sure there is only one IP listed above and it is yours.
#If not, wait a minute and try again, some a-hole bot was probably trying to hack you.
#For example, https://ipinfo.io/45.141.84.44 tried hacking into mine...If you see two IP addresses pulled from active RDP connections, do not whitelist with the next command. Otherwise, carry on!
Code:
New-NetFirewallRule -Name Allow$rdpIP -DisplayName 'Allow from myself' -Enabled True -Direction Inbound -Protocol ANY -Action Allow -Profile ANY -RemoteAddress $rdpIPCool trick to get your server IP:
Code:
ipconfig | findstr "v4" | ForEach-Object { $_.split(":")[1] } | %{$_.Trim()}According to this here, Microsoft recommends.
Code:
#On the Hyper-V host to be managed, open a Windows PowerShell session as Administrator.
#Create the necessary firewall rules for private network zones:
Enable-PSRemoting
#To allow remote access on public zones, enable firewall rules for CredSSP and WinRM:
Enable-WSManCredSSP -Role server
#For details, see Enable-PSRemoting and Enable-WSManCredSSP.
The server should be ready to go, for sure.
---
The client also requires some specific configurations like this:
Open a Windows PowerShell session as Administrator.
Make sure your current network profile is set to private, simply copy/paste:
Code:
$myNetAlias = Get-NetConnectionProfile | findstr "Alias" | ForEach-Object { $_.split(":")[1] } | %{$_.Trim()}
Set-NetConnectionProfile -InterfaceAlias $myNetAlias -NetworkCategory Private
#Time to start WinRM temporarily
Start-Service -Name winrm
#Get your list of TrustedHosts
Get-Item WSMan:\localhost\Client\TrustedHosts
#Now set this to allow everything
Set-Item WSMan:\localhost\Client\TrustedHosts -Value "*"
Stop-Service -Name winrmOpen gpedit.msc

Go to Local Computer Policy > Computer Configuration > Administrative Templates > System > Credentials Delegation
Enable "Allow delegating fresh credentials"
Enable "Allow delegating fresh credentials with NTLM-only server..."
In both of the above policy settings you enabled, add this:

wsman/*
Apply said changes, you should be all set...
Any errors? Let me know right away and I will help!! Just reply to this thread..
Skip the below, don't gaf to work w/ secedit or keep debugging through regedit messin'
---NONE OF THE FOLLOWING WORKS... HINTTTTTTTTTTTTTTTTTT::: SKIP TO THE NEXT POST IN THIS THREAD!! Just mad scientist crap is below on this specific post.. - I GIVE UP, SKIP IT.. should work fine without the below, also not responsible if it breaks ur pc lol ---
Time to edit your silly-stuff just in case, same PowerShell entry area:
Code:
#Just read the values, for giggles
Get-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\
#Setting the values to enable
Set-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\ -Name AllowFreshCredentials -Value 1
Set-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\ -Name ConcatenateDefaults_AllowFresh -Value 1
Set-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\ -Name ConcatenateDefaults_AllowFreshNTLMOnly -Value 1
Set-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\ -Name AllowFreshCredentialsWhenNTLMOnly -Value 1
#Get the TrustedHosts
Get-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentials\
Get-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\
#Getting pissed off because gpedit/regedit are not showing same values, so I set Wafflescometh in gpedit as value and now searching w/ regedit
#Found at Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly
#Matches Get-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 1
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 2
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 3
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 4
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 5
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 6
Set-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 1 -Value "wsman/*"
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentials\ -Name 1
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentials\ -Name 2
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentials\ -Name 3
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentials\ -Name 4
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentials\ -Name 5
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentials\ -Name 6
Set-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentials\ -Name 1 -Value "wsman/*"Not working, download RSAT:
Download Remote Server Administration Tools for Windows 10 from Official Microsoft Download Center
IMPORTANT: Starting with Windows 10 October 2018 Update, RSAT is included as a set of "Features on Demand" in Windows 10 itself. See "Install Instructions" below for details, and "Additional Information" for recommendations and troubleshooting. RSAT lets IT admins manage Windows Server roles and...
www.microsoft.com
Download version WindowsTH-RSAT_WS_1803-x64.msu or latest - launch - install.
Continue, accept, etc.

You will now have access to..
Group Policy editing, whoo! Turns out this only works if ur actually in a domain, many ppl probably r not lel. Need forest.. AD/DC
Code:
$myGuid = (get-wmiobject Win32_ComputerSystemProduct).UUID...
Get-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 1
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 2
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 3
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 4
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 5
Remove-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 6
Set-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 1 -Value "wsman/*"
Get-ItemProperty -Path HKLM:\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\
Remove-ItemProperty -Path HKLM:\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 1
Remove-ItemProperty -Path HKLM:\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowFreshCredentialsWhenNTLMOnly\ -Name 2
Last edited: